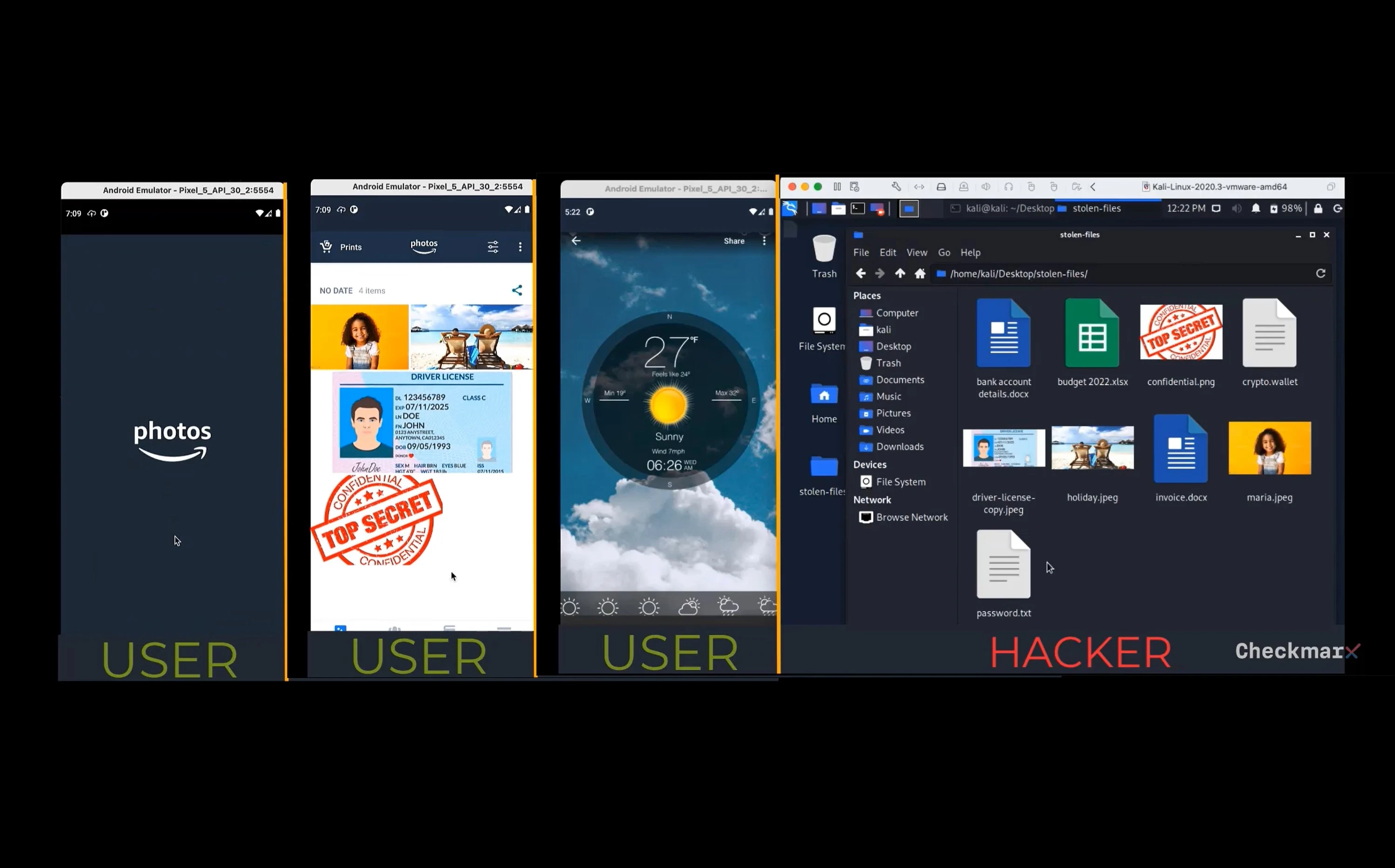
Amazon Photos is good to go as before after the company recently announced how it managed to get rid of a major vulnerability that affected the app.
Amazon Photos for Android is seen as an immensely popular app on the Google Play Store with a record of more than 50 million downloads so far.
For those who may not be aware, the app is deemed to be a storage application for both pictures and videos, which allows its users to freely share their images with an audience comprising of not more than 5 members. At the same time, it is called out for its incredible management and powerful organization too.
The recent flaw really sent shockwaves to users after it was first detected by researchers at Checkmarx. The vulnerability was found to be present in a certain element of the app and that is what led to it being manifested and forcing the file to be up for external grabs without the need for authentication.
Hence, exploitation with this bug would have given rise to different malicious apps that had been installed on a similar device so as to allow for the snatching of access tokens being used by Amazon APIs for authentication.
The worrisome factor was related to how some of these APIs had plenty of sensitive details included in them like their names, emails, and their address too. Meanwhile, those present on the Amazon Drive held user files.
The part that was most vulnerable would be launched and triggered in the form of an HTTP request which entailed a heading comprising a user’s token.
Researchers were quick to notice how any external program could launch a vulnerability while triggering requests at the same time and allowed tokens to be received to servers headed by actors.
There was a series of different scenarios under investigation using the respective token and how files on Amazon Drive managed to erase history in a way where deleted data couldn’t be recovered easily.
Hence, it makes sense why attacks were carried out with so much ease and how ransomware scenarios became all the more common with the app.
All that was now needed for the threat actor to complete his mission was the ability to eradicate the previous history while simply rewriting and comprehending the user’s files.
While the matter was first publicized to Amazon late last year by Checkmarx, we’re glad to see that it didn’t take too long for the bug to be removed, considering the fact that it was classified as being a vulnerability of high-intensity.
Read next: New Phishing Attack Uses Facebook Messenger Chatbots And Impersonates Platform’s Support Team
Amazon Photos for Android is seen as an immensely popular app on the Google Play Store with a record of more than 50 million downloads so far.
For those who may not be aware, the app is deemed to be a storage application for both pictures and videos, which allows its users to freely share their images with an audience comprising of not more than 5 members. At the same time, it is called out for its incredible management and powerful organization too.
The recent flaw really sent shockwaves to users after it was first detected by researchers at Checkmarx. The vulnerability was found to be present in a certain element of the app and that is what led to it being manifested and forcing the file to be up for external grabs without the need for authentication.
Hence, exploitation with this bug would have given rise to different malicious apps that had been installed on a similar device so as to allow for the snatching of access tokens being used by Amazon APIs for authentication.
The worrisome factor was related to how some of these APIs had plenty of sensitive details included in them like their names, emails, and their address too. Meanwhile, those present on the Amazon Drive held user files.
The part that was most vulnerable would be launched and triggered in the form of an HTTP request which entailed a heading comprising a user’s token.
Researchers were quick to notice how any external program could launch a vulnerability while triggering requests at the same time and allowed tokens to be received to servers headed by actors.
There was a series of different scenarios under investigation using the respective token and how files on Amazon Drive managed to erase history in a way where deleted data couldn’t be recovered easily.
Hence, it makes sense why attacks were carried out with so much ease and how ransomware scenarios became all the more common with the app.
All that was now needed for the threat actor to complete his mission was the ability to eradicate the previous history while simply rewriting and comprehending the user’s files.
While the matter was first publicized to Amazon late last year by Checkmarx, we’re glad to see that it didn’t take too long for the bug to be removed, considering the fact that it was classified as being a vulnerability of high-intensity.
Read next: New Phishing Attack Uses Facebook Messenger Chatbots And Impersonates Platform’s Support Team