Apps that can allow people to transfer payments through their mobile phones have revolutionized the financial sector, with some experts estimating that around 4.8 million transactions will be conducted in 2025. By 2028, the total value of transactions is set to surpass the $16 trillion dollar mark, but how safe are these apps exactly?
In order to get to the bottom of this all important question, Norwegian app security firm Promon closely studied 73 of the most popular payment apps around the world. They analyzed their security protocols and how susceptible they were to various kinds of malware, and it turns out that the vast majority of them are not quite as safe as you might’ve hoped.
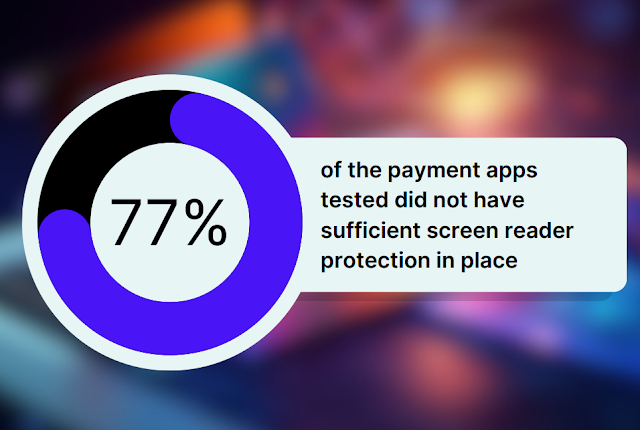
Based on the findings presented in this study, a whopping 77% of these apps didn’t have adequate protection for screen readers and the like. As a result, they were particularly at risk of being compromised through malware that can exfiltrate data. Six of these apps, representing 8.2% of the overall sample size, went so far as to log usernames if screen readers were used, which made them even more prone to exfiltration attacks.
One thing that bears mentioning here is that this is still only a partial vulnerability, since passwords weren’t compromised quite as easily during the simulated exfiltrations that were conducted as part of this study. However, just 4.1% of all apps had defense mechanisms that were comprehensive enough to withstand the strongest of malware attacks.
Considering the massive size of this industry, as well as the rapid rate of growth that it has been seeing as of late, it is imperative that the companies behind these platforms take steps to plug their security issues. Screen reader detection is a must have for these apps, otherwise the propensity for financial loss will be far too high, and many consumers might not be willing to take the enormous risk that they represent.
Threats are evolving just as quickly these apps, so it is also essential that developers utilize app shielding as and when possible. Combining a variety of security protocols can make them robust enough to provide the amount of protection that customers have come to expect. Falling short of these requirements could lead to attacks becoming all the more widespread, and it will be interesting to see how developers tackle these issues over the next few years.
Read next: What would be the global financial toll of a 24-hour Internet blackout?
In order to get to the bottom of this all important question, Norwegian app security firm Promon closely studied 73 of the most popular payment apps around the world. They analyzed their security protocols and how susceptible they were to various kinds of malware, and it turns out that the vast majority of them are not quite as safe as you might’ve hoped.
Based on the findings presented in this study, a whopping 77% of these apps didn’t have adequate protection for screen readers and the like. As a result, they were particularly at risk of being compromised through malware that can exfiltrate data. Six of these apps, representing 8.2% of the overall sample size, went so far as to log usernames if screen readers were used, which made them even more prone to exfiltration attacks.
One thing that bears mentioning here is that this is still only a partial vulnerability, since passwords weren’t compromised quite as easily during the simulated exfiltrations that were conducted as part of this study. However, just 4.1% of all apps had defense mechanisms that were comprehensive enough to withstand the strongest of malware attacks.
Considering the massive size of this industry, as well as the rapid rate of growth that it has been seeing as of late, it is imperative that the companies behind these platforms take steps to plug their security issues. Screen reader detection is a must have for these apps, otherwise the propensity for financial loss will be far too high, and many consumers might not be willing to take the enormous risk that they represent.
Threats are evolving just as quickly these apps, so it is also essential that developers utilize app shielding as and when possible. Combining a variety of security protocols can make them robust enough to provide the amount of protection that customers have come to expect. Falling short of these requirements could lead to attacks becoming all the more widespread, and it will be interesting to see how developers tackle these issues over the next few years.
Read next: What would be the global financial toll of a 24-hour Internet blackout?