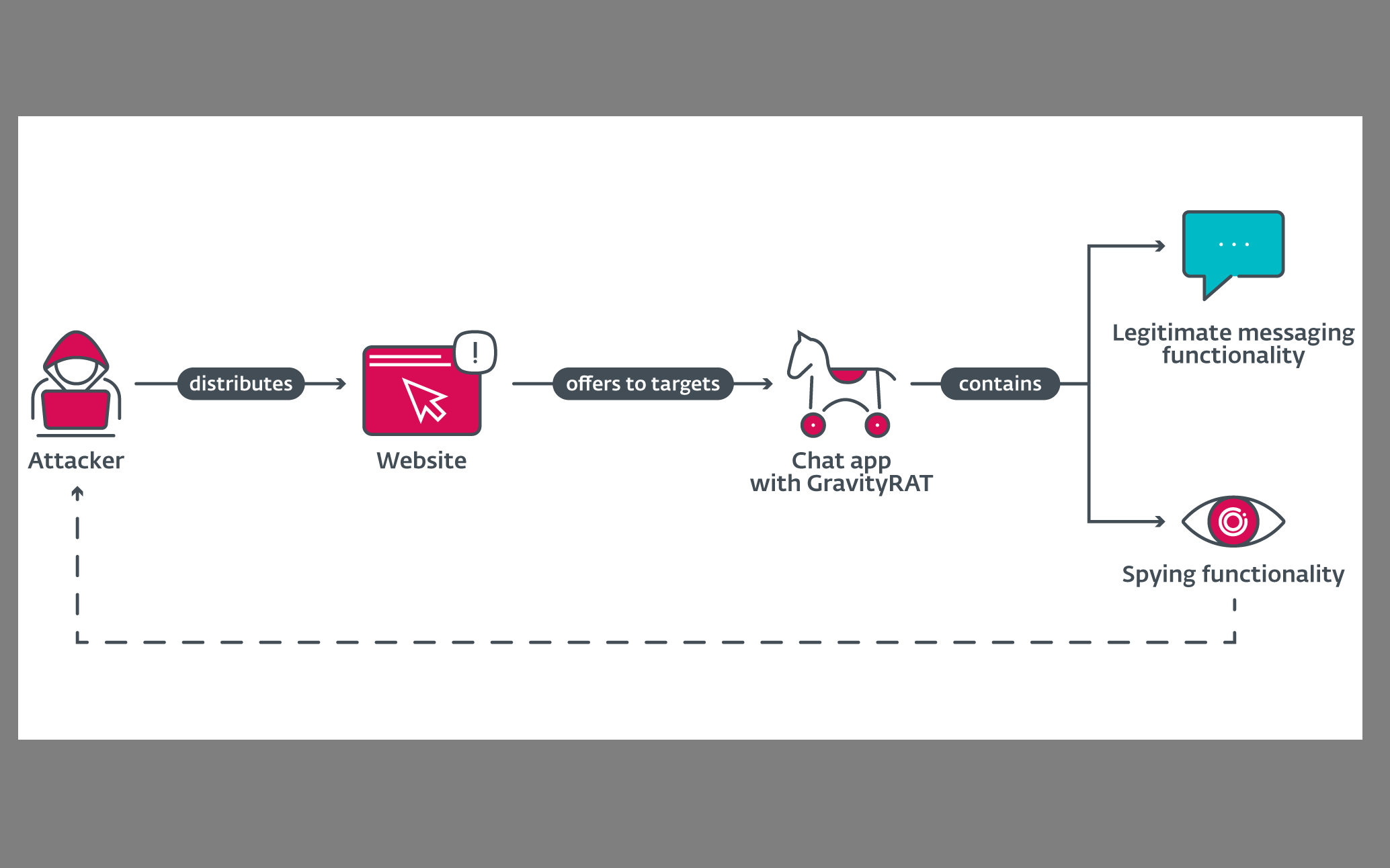
A new campaign involving Android malware has surfaced, propagating the most recent iteration of GravityRAT since August 2022. The objective of this campaign is to infiltrate mobile devices through a chat application known as 'BingeChat,' which has been modified with malicious intent to pilfer data from specific victims.
GravityRAT, an established malware that has been active since at least 2015, has primarily targeted platforms other than Android. However, in 2020, its operators known as 'SpaceCobra' began focusing on Android devices. Now, with the latest version of GravityRAT, the malware has added a new feature: the ability to pilfer WhatsApp backup files.
WhatsApp backups are designed to assist users in seamlessly transferring the users' media files, message history, and data to different devices. These backups frequently contain valuable and sensitive information, such as unencrypted documents, videos, text, and photos. By exploiting this vulnerability, the GravityRAT malware presents a significant threat to the security of users' personal data.
The campaign on Android revolves around the dissemination of a chat application called 'BingeChat.' This application asserts that it provides comprehensive encryption and showcases a user-friendly interface accompanied by advanced functionalities. In order to utilize the application, individuals must navigate to the designated website, "bingechat[.]net," or other plausible domains and distribution channels. However, obtaining the application is contingent on receiving an invitation, which requires verifiable credentials or the setup of a new account.
By implementing a restricted registration system, the malicious actors gain the ability to carefully choose the recipients for the infected app, thereby complicating the task of security researchers who aim to obtain and examine a copy of the malware.
SpaceCobra, the group behind GravityRAT, has previously employed a similar tactic of promoting malicious Android APKs to target victims. In the past, they utilized chat apps such as 'SoSafe' and 'Travel Mate Pro' to execute their campaigns.
After thorough analysis, cybersecurity experts have discovered that the deceptive application called 'BingeChat' is, in fact, a modified iteration of OMEMO IM, a legitimate open-source instant messaging app designed for Android devices. Extensive research conducted by ESET's team unveiled that the group behind GravityRAT, known as SpaceCobra, leveraged OMEMO IM as the base of this other deceitful application called "Chatico." This specific version of the malware was deliberately disseminated to select individuals in the period of summer during the year 2022, making use of the defunct domain "chatico.co[.]UK."
During the installation process, BingeChat seeks various permissions from users, such as accessing location, phone, contacts, texts, storage, etc. By imitating the permissions typically requested by legitimate instant messaging applications, BingeChat attempts to avoid raising suspicion.
Prior to any signing up process, BingeChat automatically transmits personal information such as contact lists, device details, SMS messages, device location, and call logs to the control and command server controlled by threat actors. Furthermore, the app illicitly acquires media and document files with various extensions, including log, png, jpg, doc, docx, opus, crypt, and more. Significantly, the file extensions associated with encrypted files align with backups from WhatsApp Messenger, presenting a substantial threat to users' sensitive data.
Importantly, the file extensions associated with encrypted files align with backups created by WhatsApp Messenger, presenting a threat to sensitive information: "delete all contacts," "delete all call logs," and "delete all files" (of a specified extension). With these commands, threat actors can exert greater control over compromised devices and eliminate critical data.
While SpaceCobra's campaigns typically target specific individuals within India, all Android users are advised to exercise caution and refrain from downloading APKs from unofficial sources other than the Google Play Store. Google claims it security system protects Android users from apps containing GravityRAT malware even when those apps come from other sources or app stores. However, it is imperative to remain vigilant when granting permissions to any app during the installation process, as this can help mitigate the risks associated with potential malware attacks.
Read next: Reducing Social Media Usage to Half Hour Decreases Mental Health Symptoms in Young Adults
GravityRAT, an established malware that has been active since at least 2015, has primarily targeted platforms other than Android. However, in 2020, its operators known as 'SpaceCobra' began focusing on Android devices. Now, with the latest version of GravityRAT, the malware has added a new feature: the ability to pilfer WhatsApp backup files.
WhatsApp backups are designed to assist users in seamlessly transferring the users' media files, message history, and data to different devices. These backups frequently contain valuable and sensitive information, such as unencrypted documents, videos, text, and photos. By exploiting this vulnerability, the GravityRAT malware presents a significant threat to the security of users' personal data.
The campaign on Android revolves around the dissemination of a chat application called 'BingeChat.' This application asserts that it provides comprehensive encryption and showcases a user-friendly interface accompanied by advanced functionalities. In order to utilize the application, individuals must navigate to the designated website, "bingechat[.]net," or other plausible domains and distribution channels. However, obtaining the application is contingent on receiving an invitation, which requires verifiable credentials or the setup of a new account.
By implementing a restricted registration system, the malicious actors gain the ability to carefully choose the recipients for the infected app, thereby complicating the task of security researchers who aim to obtain and examine a copy of the malware.
SpaceCobra, the group behind GravityRAT, has previously employed a similar tactic of promoting malicious Android APKs to target victims. In the past, they utilized chat apps such as 'SoSafe' and 'Travel Mate Pro' to execute their campaigns.
After thorough analysis, cybersecurity experts have discovered that the deceptive application called 'BingeChat' is, in fact, a modified iteration of OMEMO IM, a legitimate open-source instant messaging app designed for Android devices. Extensive research conducted by ESET's team unveiled that the group behind GravityRAT, known as SpaceCobra, leveraged OMEMO IM as the base of this other deceitful application called "Chatico." This specific version of the malware was deliberately disseminated to select individuals in the period of summer during the year 2022, making use of the defunct domain "chatico.co[.]UK."
During the installation process, BingeChat seeks various permissions from users, such as accessing location, phone, contacts, texts, storage, etc. By imitating the permissions typically requested by legitimate instant messaging applications, BingeChat attempts to avoid raising suspicion.
Prior to any signing up process, BingeChat automatically transmits personal information such as contact lists, device details, SMS messages, device location, and call logs to the control and command server controlled by threat actors. Furthermore, the app illicitly acquires media and document files with various extensions, including log, png, jpg, doc, docx, opus, crypt, and more. Significantly, the file extensions associated with encrypted files align with backups from WhatsApp Messenger, presenting a substantial threat to users' sensitive data.
Importantly, the file extensions associated with encrypted files align with backups created by WhatsApp Messenger, presenting a threat to sensitive information: "delete all contacts," "delete all call logs," and "delete all files" (of a specified extension). With these commands, threat actors can exert greater control over compromised devices and eliminate critical data.
While SpaceCobra's campaigns typically target specific individuals within India, all Android users are advised to exercise caution and refrain from downloading APKs from unofficial sources other than the Google Play Store. Google claims it security system protects Android users from apps containing GravityRAT malware even when those apps come from other sources or app stores. However, it is imperative to remain vigilant when granting permissions to any app during the installation process, as this can help mitigate the risks associated with potential malware attacks.
Read next: Reducing Social Media Usage to Half Hour Decreases Mental Health Symptoms in Young Adults