Being connected to the internet is obviously important because of the fact that this is the sort of thing that could potentially end up allowing you to access a lot of information, but in spite of the fact that this is the case WiFi internet can create a lot of security issues as well. A new drone has been developed that might enable malicious actors to capitalize on security flaws in Wi-Fi connections and hack people’s accounts through their own walls.
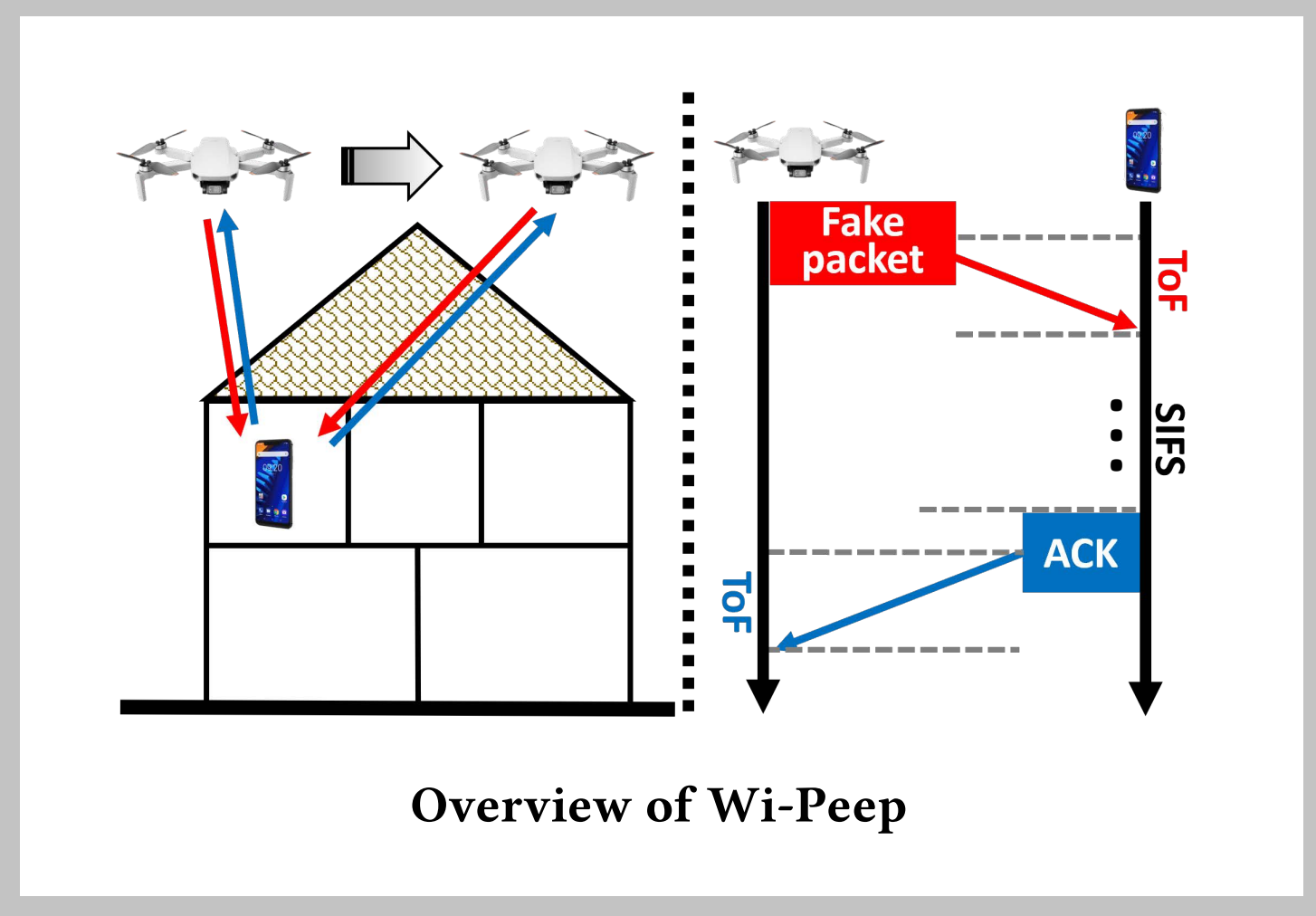
This information comes from the University of Waterloo, and with all of that having been said and now out of the way it is important to note that it draws attention to a device known as Wi-Peep. It’s a consumer drone that has been altered significantly to manipulate a vulnerability known as Polite Wi-Fi. This can facilitate location tracking to a highly accurate degree, and that can make internet connections a lot less secure than might have been the case otherwise.
The polite Wi-Fi protocol allows malicious actors to circumvent refused connections to smart devices with all things having been considered and taken into account. The hackers then use the Wi-Peep device to send a constant stream of messages to the device which can enable them to track user locations with lots of accuracy. They might be able to use this to track security guard movements in restricted areas such as banks, as well as find homes that are easy to break into by hacking into laptops and security cameras to conduct surveillance before making their attempt.
The revelation of this new vulnerability can send shockwaves throughout the industry, and Wi-Fi chip manufacturers might be able to make a modification that can make such attacks less of an issue. They can make response times randomized which can decrease the accuracy of location detection using this method. This also casts some doubts over the safety of IoT devices which are becoming all the more prevalent and may give malicious actors a greater number of access points that they can use to conduct their various criminal and illicit activities.
Read next: After A Supply Chain Attack, Hundreds Of Online News Sites In the US Are Spreading Malware Around
This information comes from the University of Waterloo, and with all of that having been said and now out of the way it is important to note that it draws attention to a device known as Wi-Peep. It’s a consumer drone that has been altered significantly to manipulate a vulnerability known as Polite Wi-Fi. This can facilitate location tracking to a highly accurate degree, and that can make internet connections a lot less secure than might have been the case otherwise.
The polite Wi-Fi protocol allows malicious actors to circumvent refused connections to smart devices with all things having been considered and taken into account. The hackers then use the Wi-Peep device to send a constant stream of messages to the device which can enable them to track user locations with lots of accuracy. They might be able to use this to track security guard movements in restricted areas such as banks, as well as find homes that are easy to break into by hacking into laptops and security cameras to conduct surveillance before making their attempt.
The revelation of this new vulnerability can send shockwaves throughout the industry, and Wi-Fi chip manufacturers might be able to make a modification that can make such attacks less of an issue. They can make response times randomized which can decrease the accuracy of location detection using this method. This also casts some doubts over the safety of IoT devices which are becoming all the more prevalent and may give malicious actors a greater number of access points that they can use to conduct their various criminal and illicit activities.
Read next: After A Supply Chain Attack, Hundreds Of Online News Sites In the US Are Spreading Malware Around